Cybercriminals target new businesses daily by looking for unprepared networks and unsuspecting employees. Yikes!
How protected is your company from a cyber attack or data breach? Articles like (9 major cyber attacks in one month) worry owners who are looking to beef up their security.
Luckily, the world of threat intelligence has made it possible for businesses to strengthen their systems, avoid being an easy target, and learn how to detect potential weak points.
So let’s explore some top-rated threat intelligence platforms that can help to defend businesses and proactively look for threats. Integrating one into your workplace could better protect your data and reduce your risk of an attack!
What Are Threat Intelligence Platforms?

Let’s start with a short definition.
Threat intelligence platforms are tools that gather external threat data in one location so security teams can more easily identify or respond to potential criminal activity.
They optimize communication between all stakeholders, including threat intelligence teams, IT professionals and security staff.
Incident response protocols are easier to manage with a single platform that connects users to established processes and accurate data.
🔎 Need some help finding the right tool?Jump to our favorites to take a deeper dive into threat intelligence:
|
Top 8 Threat Intelligence Platforms for Cyberattack Prevention
Simplify your team’s intelligence data gathering with one of the leading cyber security platforms. Comparing your options will connect you with the best threat tools for your needs and budget.
1. ThreatConnect
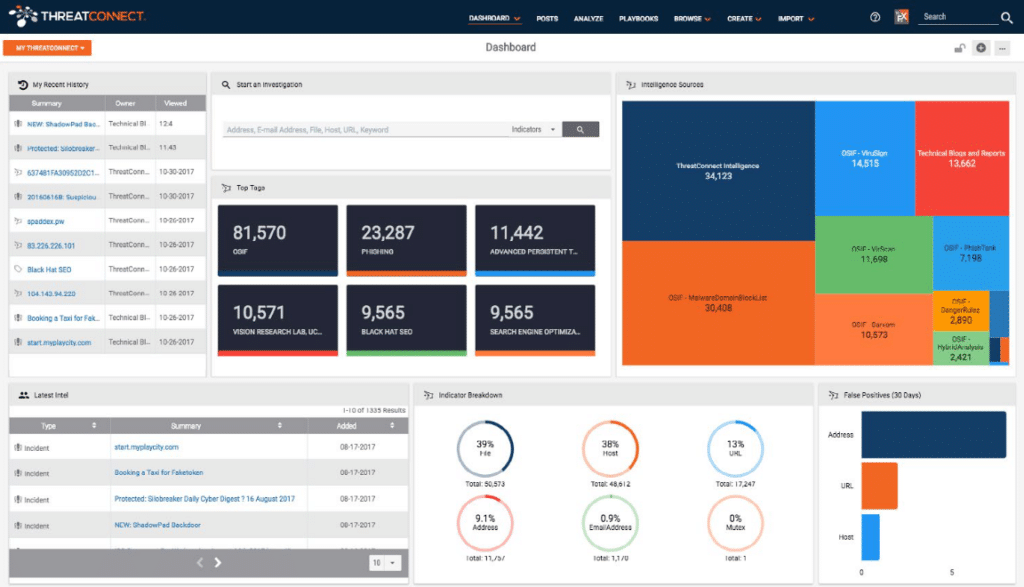
ThreatConnect is leading the threat intelligence platform market. The product collects data from commercial and open-source third-party feeds.
Advanced automation and orchestration turn the data into actionable intelligence, even for inexperienced team members. Security operations professionals can take action against threats with precise information from every indicator of compromise (IoC).
Call to schedule a demo and get a quote to understand how ThreatConnect helps companies prevent cyberattacks through risk quantification and threat intelligence.
🏅 Why we love this threat intelligence tool: ThreatConnect is a flexible, scalable platform that grows with businesses without compromising their digital security.
⭐ Standout Features:
- ❇️ Robust ecosystem integration capabilities: ThreatConnect works alongside numerous firewalls, security information and event management (SIEM) systems, and other security tools. Your collected data can come from third-party feeds and an existing diverse security infrastructure.
- ❇️ AI-powered assistance: The CAL feature allows users to get deeper insights, visual graphs and report summaries without requiring more time from their schedules.
- ❇️ Cyber risk quantification: Every noted threat is accompanied by a financial analysis demonstrating the potential cost of lax security measures against IoCs.
G2 | Capterra | Gartner |
Here is a customer review from Gartner:
“The experience with ThreatConnect has been overwhelmingly positive. I find the platform to be very good as a security professional. One of the most impressive aspects of ThreatConnect is its comprehensive suite of features. The platform provides a wide range of capabilities, from analysis and response automation to threat intelligence aggregation. ThreatConnect’s user interface is simple & user-friendly, making it easy to navigate and leverage its robust features effectively.”
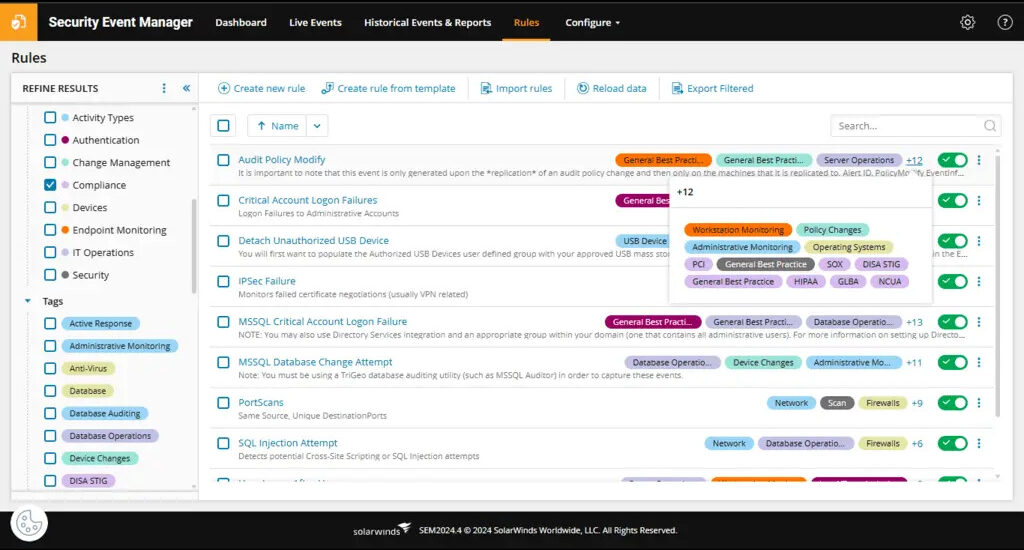
2. SolarWinds Security Event Manager
The SolarWinds Security Event Manager is among the most popular security event logging platforms. Users enjoy fast detection and response solutions, integration capabilities and numerous firewall programs.
If you are interested in standard security measures with an easy-to-use interface, the SolarWinds threat intelligence tool could be helpful.
🏅 Why we love this threat intelligence tool: Users get 24/7 customer service support through phone and email.
⭐ Standout Features:
- ❇️ Extended free trial: You can try the platform for a month before deciding whether to purchase it.
- ❇️ Customizable threat reports: Authorized users can customize reports in written or visualized formats to understand threat data.
- ❇️ Business-specific automation: If your team frequently deals with the same threats, Security Event Manager allows for configured fixes designed for those threats.
G2 | Capterra | Gartner |
Here is a customer review from G2:
“SolarWinds security is a ready to use affordable solution … from network monitoring to your device monitoring. Alerts and analysis at one clear dashboard. The event manager is easy to understand and customised suited to your specific organization needs.”
3. Rapid7 Threat Command
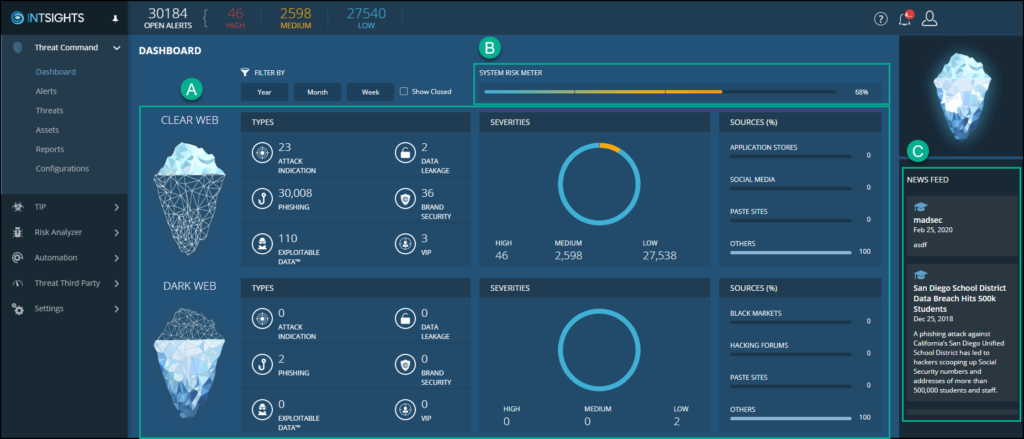
Business owners needing intensive security monitoring often rely on Rapid7 Threat Command.
The platform prioritizes specific IoCs depending on your preferences, scores threats and integrates easily with other Rapid7 programs. You can also connect it with open-source intelligence feeds for more in-depth information about potential threats to your business.
🏅 Why we love this threat intelligence tool: The Threat Command platform displays web and dark web threats so users clearly understand where potential attacks are coming from.
⭐ Standout Features:
- ❇️ Available training materials: You might not have to create independent training modules for your team because Threat Command has documentation and videos for new users.
- ❇️ System risk meter: The risk meter on the dashboard allows you to understand your business’s security at a glance.
- ❇️ Varying report formats: Numerous report forms are included, like leaked credentials, network types and executive summaries.
G2 | Capterra | Gartner |
Here is one user’s review of Threat Command:
“Everything can be found in just place yet easily identifiable. It is very easy to add a new system and run the scans. It shows deep insights into the vulnerabilities found in the network and how to remediate them.”
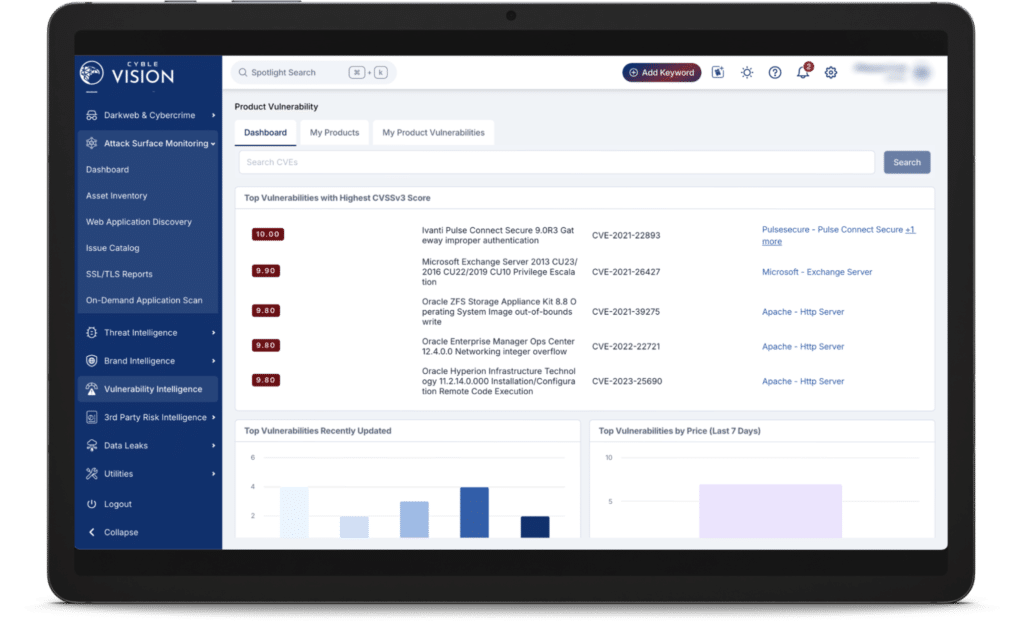
4. Cyble Vision
The Cyble Vision platform primarily provides digital risk protection from threats outside of your network.
Users appreciate its deep web and dark web monitoring and its ability to crawl underground forums for stolen credentials or data leaks.
You will get early breach detection alerts regarding your protected data and brand monitoring capabilities to stop harmful events like brand impersonation.
🏅 Why we love this threat intelligence tool: Cyble Vision is one of the top threat intelligence platforms for combined dark web and brand protection monitoring.
⭐ Standout Features:
- ❇️ AI threat hunting: Your Cyble Vision platform will use machine learning and AI to automate finding your business’s most pressing threats.
- ❇️ Personalized support: Cyble Vision users enjoy customized service whenever they need help.
- ❇️ Various threat platform monitoring: Users get threat alerts from multiple types of platforms, including app stores, websites and forums.
G2 | Gartner | Trustpilot |
Check out this positive review:
“Our overall experience with Cyble Vision has been extremely positive. This has enhanced our TI capabilities. Customer support has been highly responsive in addressing queries and recommendations.
Post implementation experience has exceeded our expectations and has become a critical part of our cybersecurity operations.”
5. Anomali ThreatStream
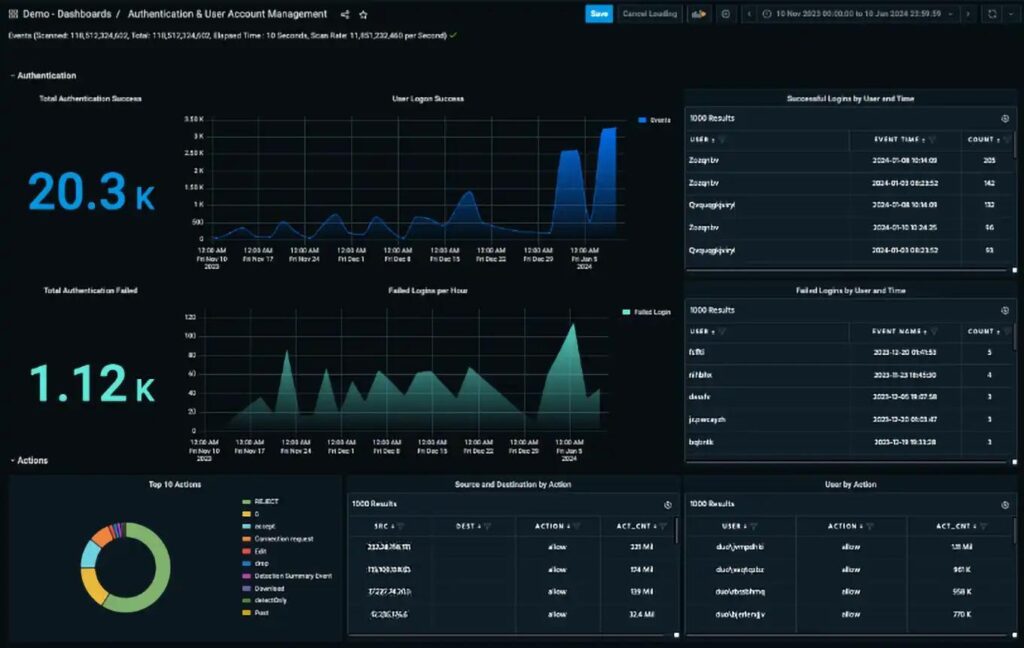
Anomali ThreatStream works with users to identify and resolve breaches. After receiving real-time IoCs, security analysts get suggestions to stop criminal activity and repair their network.
ThreatStream sources information from over 100 open-source feeds, giving you comprehensive digital protection.
🏅 Why we love this threat intelligence tool: This flexible platform can be installed on-premise, as software-as-a-service or within an air-gapped network.
⭐ Standout Features:
- ❇️ Included training materials: Users gain access to Anomali University, which gives team leaders everything they need to show analysts how to use the platform.
- ❇️ Possible sandbox investigations: ThreatStream provides a sandbox tool, so your team can dismantle and study threats.
- ❇️ Easy integrations: ThreatStream integrates with existing firewalls, SIEM tools and endpoint detection and response platforms.
G2 | Gartner | Trustpilot |
Devin Ertel @ Blackhawk Network Holdings at this to say about Anomali:
“Before Anomali, we had tons of information without context. We had to look through thousands of alerts quickly just to see what stood out and then react to those. Anomali enabled us to spend less time dealing with noise, and more time focusing on critical issues.”
6. CrowdStrike Adversary Intelligence
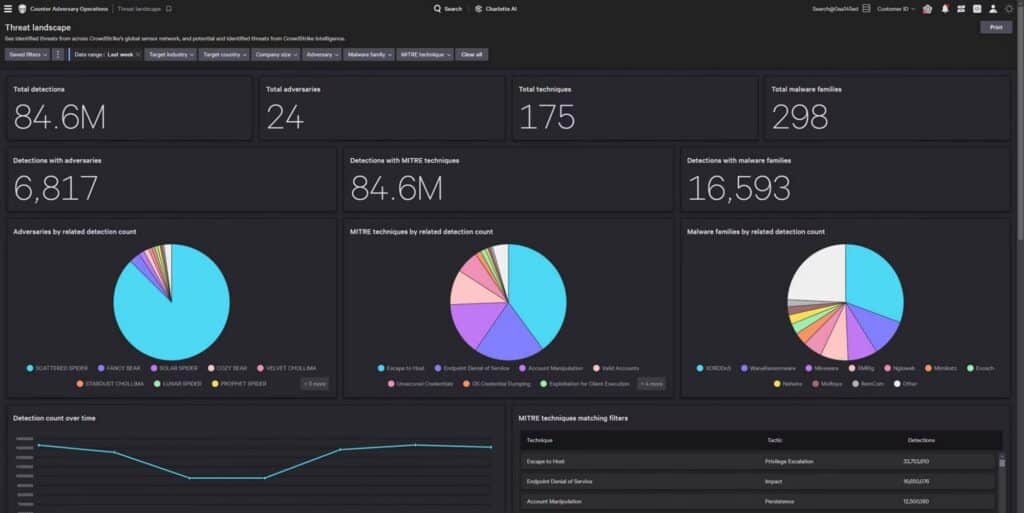
Threat analysts wanting to track and profile threat actors should consider the CrowdStrike Adversary Intelligence program.
The platform takes an adversary-centric approach to security by providing worldwide endpoints for unparalleled threat visibility. You will receive alerts for specific threat actors and curate detailed profiles to understand influencing factors like their motivations and preferred targets.
This unique approach to threat detection makes the Adversary Intelligence program one of the best cyber threat intelligence platforms available.
🏅 Why we love this threat intelligence tool: Authorized users can create customizable threat feeds based on their geographic location or industry for more targeted alerts.
⭐ Standout Features:
- ❇️ Explanation of the why: Instead of only showing how a threat could affect your network, Adversary Intelligence teaches you why the person behind the threat is targeting you to guide you toward more effective long-term security solutions.
- ❇️ Seamless Falcon integration: The Adversary Intelligence program builds on CrowdStrike’s Falcon Managed Detection and Response platform.
- ❇️ Faster detection times: Combining global domains and automated investigation tools accelerates your network security efforts.
G2 | Capterra | Trustpilot |
Kelly McCracken, SVP of Detection and Response @ Salesforce shared this review of Crowdstrike:
“Having a partner that can help you dig in and really investigate and have that threat intelligence to back it up to say ‘actually this is not what you think it is’, has definitely helped. I can take a deep breath when I hear ‘we’ve checked with CrowdStrike. It’s okay’, and that has given me peace of mind.”
7. Google Cloud Threat Intelligence
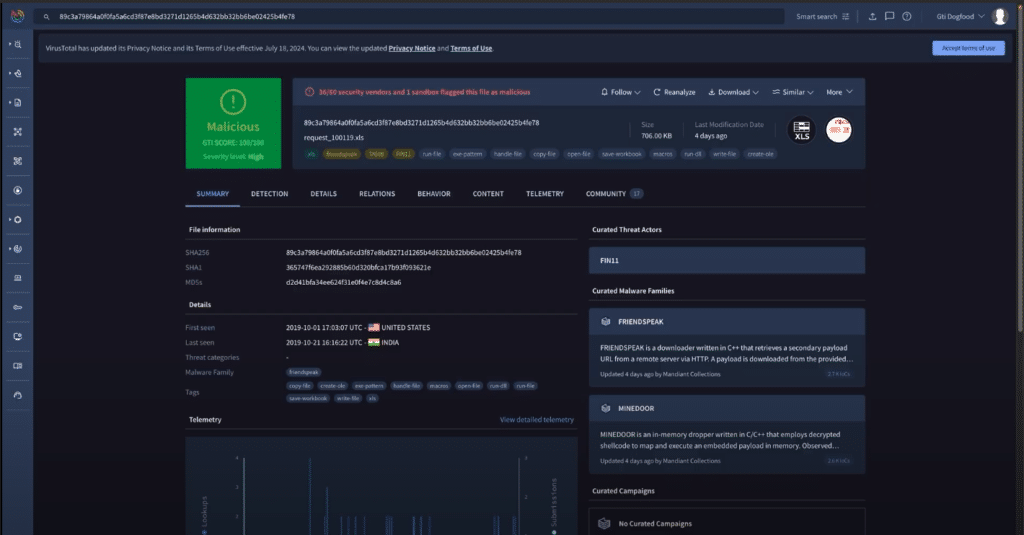
Security operations professionals might know the Google Cloud Threat Intelligence platform as Mandiant Advantage. Google bought the program and enhanced it with better attack surface management tools.
You will get open-source intelligence indicators, vulnerability data and threat actor information on your dashboard. 24/7 customer service support also comes with the enterprise plan.
🏅 Why we love this threat intelligence tool: Threat Intelligence remains on Google’s cloud, so you will not have to utilize any storage space to install the platform.
⭐ Standout Features:
- ❇️ Global red flag detection: Users can identify threats with location and industry filters that populate information from worldwide sources.
- ❇️ Google-level data reach: Threat Intelligence users tap in to Google’s industry-leading data sources for unparalleled threat visibility.
- ❇️ Cloud threat alerts: You will bolster your cloud network security with Threat Intelligence’s cloud-specific features for issues like compromised accounts or misconfigured resources that leave your network vulnerable.
G2 | Capterra | Trustpilot |
Check out this review from an IT Manager on Gartner:
“It is a pretty robust solution which helps you find detailed information about threat actors and tactics used by them.
One of the best in my opinion is the monitoring information on [the] dark web and [it] also provide[s] information regarding [the] current threat landscape in the form of detailed reports.”
👉 Try Google Cloud Threat Intelligence
8. Recorded Future
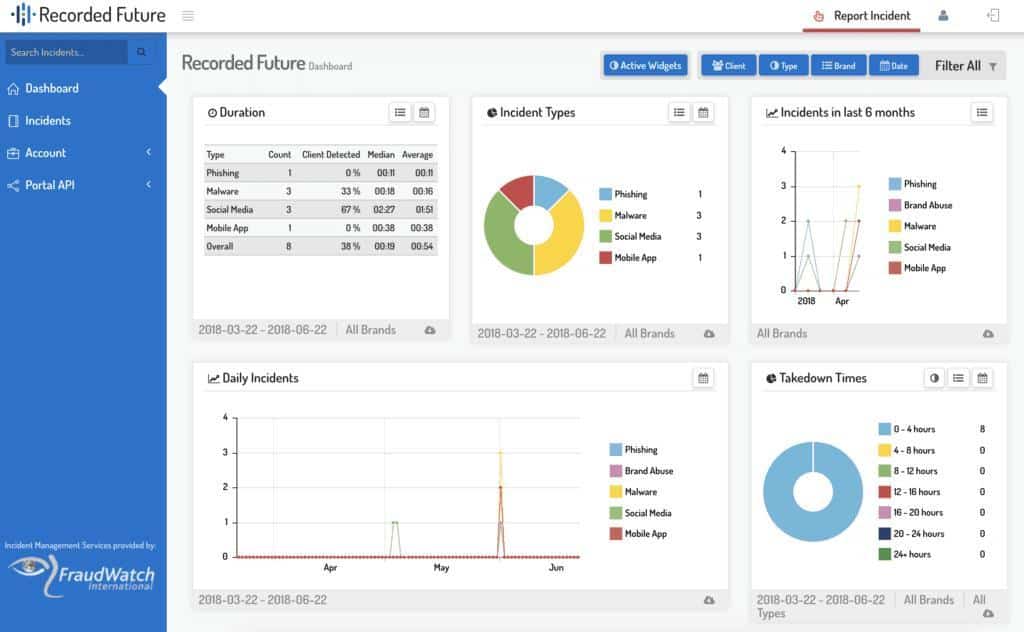
Recorded Future could fit your network security needs well if you have a smaller team. The platform uses its Intelligence Graph to collect and showcase threat data for smaller groups of authorized users.
When you are not using its attack mapping and threat scoring features, you can use the free browser extension included with the platform to get extra web security without paying an additional fee.
🏅 Why we love this threat intelligence tool: Like the best threat intelligence platforms, Recorded Future offers users sandbox tools to explore threats in depth.
⭐ Standout Features:
- ❇️ API detection capabilities: Recorded Future is flexible, so users can download numerous detection rules to better identify and solve threats.
- ❇️ Correlation-showing dashboards: You can quickly identify security trends by seeing correlations between red flags or attacks on your dashboard.
- ❇️ Alerts from across the web: Authorized users get threat alerts from the dark web and social media for more comprehensive security coverage.
G2 | Gartner | Trustpilot |
Kyriba Security Engineer, Alex Minster, had this to say about the software tool:
“Threat intelligence from Recorded Future makes our team look prophetic.
We’re able to say, ‘Here’s something we need to be worrying about so let’s raise awareness around that,’ and sure enough, it starts to land on our shores a month or so later.”
Key Advantages of Using Threat Intelligence Platforms
People turn to threat tools when they need specific advantages to protect their businesses better. Learning about those benefits could help you decide whether now is the best time to start using a similar platform.
1 Real-Time Detection
Threat intelligence is a 24/7 job. People used to pull potential threat data from numerous sources manually, but threat intelligence platforms automate the job. Authorized users can spend their time monitoring what the platform collects and alert people if they spot vulnerabilities. Faster, continual data collection is essential for professional teams.
2 Predictive Insights
Threat detection platforms look for active threats and log anything they find. The software reviews data regularly to form trend reports. Every day, around 500 million phishing emails appear in inboxes. If that is the most common way cybercriminals are trying to enter your network, you will get more accurate predictions based on business-specific incidents.
3 Automated Responses to Cyber Threats
Responding to every security task manually takes time. Your team might spend hours updating every employee’s computer firewall or isolating infected systems after an attack. They could use that time to strengthen your network instead. Threat intelligence platforms automate time-consuming processes so your security team can focus on other essential tasks.
4 Employee Education
People often undergo annual employee training to learn how to spot a phishing email, create strong passwords and use other basic digital security strategies.
Threat intelligence tools make education more useful by providing information for team leaders. Managers can customize their presentations according to their business’s previous threats or security lapses, giving people the precise security information they need.
How to Implement Threat Intelligence Platforms
If you are new to threat intelligence tools, you might encounter some common challenges when integrating one into your workplace. Use some key strategies to navigate those moments with ease.
Avoid Data Overload and False Positives

Threat tools pull data from numerous places, like open-source intelligence feeds. Establishing your chosen platform with too many feeds could result in data overload. Your tool may also send too many alerts for things that are not actual threats — over half the alerts a security team receives are false positives.
Filtering your data, prioritizing feeds and using relevant sources of information could prevent those complications. If you are unsure what that would require, the installation team or your threat intelligence analysts can assist you.
Integrate With an Existing Security Infrastructure

If your business already has digital security measures in place, it is crucial to integrate them with your chosen threat detection tool. Using previously established ones will make the data flow smoother and strengthen those measures.
Existing firewalls will not deal with potential threats if your new tool monitors their activity in addition to their virtual defense.
Budget for the Costs

Considering the average data breach cost was $9.36 million per business in 2024, expenses related to threat intelligence platforms could be significantly less than a potential cyberattack.
Requesting quotes is the best way to get the most accurate financial information. Work with those estimations to see which tool is best for your budget.
Strategies for Maximizing Effectiveness with Threat Intelligence
Even when you feel confident about your chosen threat detection tool, there will be ways to improve your experience as time passes. Remember a few strategies to make your investment an even better decision for your team.
1. Cultivate Actionable Data
Identify the indicators of compromise that are most relevant to your business. Make those a data collection priority and require context from both external and internal sources.
The extra information will clarify potential threats while pointing out optimal response efforts based on your team’s next-step guidance.
2. Create a Clear Use Strategy
Cyber threat intelligence platforms are most useful when security analysts have outlined use-and-response steps. Define your objectives — like faster incident response times — before using the threat intelligence platform.
Outline the authorized users for the program and the people they should contact if an incident occurs.
Users should also know how to share the threat intelligence through their preferred or encrypted communication channels.
Senior officials with the FBI recently urged Americans to communicate over encrypted channels because they are challenging to hack. Doing the same with your team’s security conversations could give you more peace of mind.
3. Find Ways to Improve Your Processes
Everyone using your threat detection tool should know which key metrics it tracks to see if your investment is paying off.
Those could be incident response times, false positive flags or the number of thwarted attacks in a set period. Request recurring feedback and schedule reviews to double-check that those processes work as intended.
Your team will adapt alongside your business’s most pressing concerns and maximize the benefits of your investment.
People Also Ask These Questions About Threat Intelligence Tools
Q: What Are the Best Threat Intelligence Platforms?
- A: The best threat intelligence platforms match your business’s specific needs, team size and budget. They should collect data from open source and commercial feeds, provide indicators of compromise for potential attacks and streamline collaboration across systems threat intelligence analysts.
Q: What Are the Three Types of Threat Intelligence Data?
- A: The three types of threat intelligence data are strategic, tactical and operational. They indicate the sophisticated levels of cybersecurity data you are getting and what that information does. Strategic data is the foundation of high-level assessments that change team-wide plans or strategies. Tactical data is the real-time information your cybersecurity measures gather, especially during attacks. Operational intelligence is the middle ground of the three, providing information on how a threat actor operates and their potential next steps.
Q: Does Threat Intelligence Require Coding?
- A: Threat intelligence does not require coding if you are using an established platform. More advanced threat detection analysts could use basic scripting skills to customize certain features, but that is not necessary when using a finished threat intelligence product.
Q: How Much Does a Threat Intelligence Platform Cost?
- A: Threat intelligence platforms cost businesses different amounts based on the organization’s size and threat risk. Requesting quotes is the best way to get more accurate information about each platform.
Q: What Is an Example of Threat Intelligence?
- A: Malicious IP addresses are an example of threat intelligence. They indicate compromised data and point to the threat actor by connecting the user with the IP address. They are much easier to pinpoint, block and manage with valuable tools like threat detection programs.